Are Age Verification Laws in the U.S. a Threat to Digital Freedom?
Introduction Age verification laws in the U.S. have become a topic of debate and controversy in recent years. These laws aim to protect minors from accessing adult content online by requiring websites to verify the age of their users. While…
How to Choose the Perfect Router for Your Home
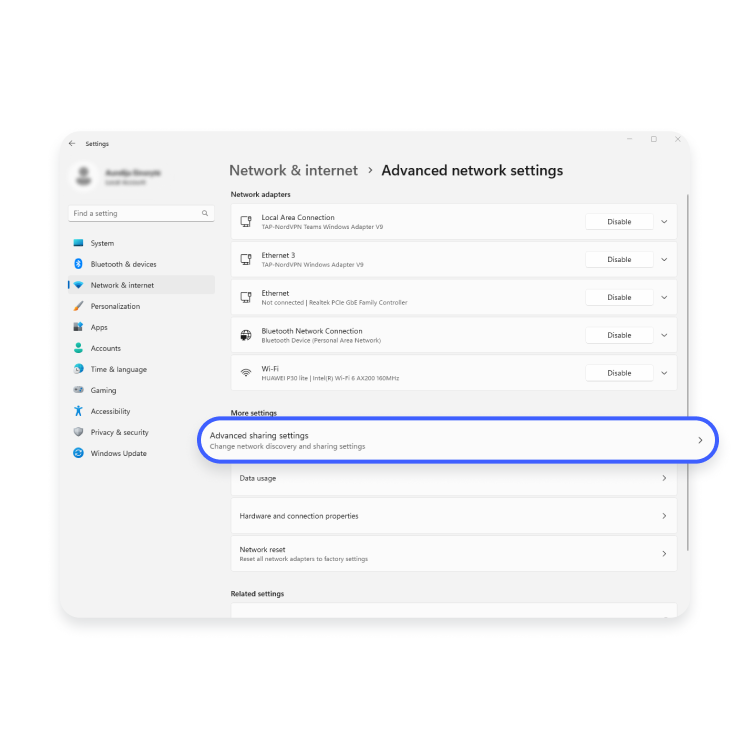
Identifying Your Needs Before choosing a router for your home, it’s important to identify your specific needs and requirements. Consider the following factors: The Router’s Purpose What will be your primary use for Wi-Fi? Different activities require different levels of…

LATEST VPN REVIEWS
LATEST VPN GUIDES
Here’s Why You Should Always Read the Privacy Policy Before Choosing a VPN
People choose to use VPNs for a wide range of reasons, from expats who want to access their home country content – newspapers, media streaming sites, online radio – while…
How ISPs Sell Your Data (and How to Stop Them)
At home, in your work environment or even at a café, you want privacy while browsing the world wide web. You don’t necessarily have to be doing something terrible or…
Here’s Why You Can’t Trust a Free VPN
A lot of internet users still don’t understand and appreciate the importance of using a VPN. There are tons of reasons why people should be connected to a VPN service. Ideally,…
How to Get a Free VPN Trial
During the period of our existence, VPN Creative has reviewed 200+ VPN providers and found the best VPN with the longest free trial period. A VPN trial is great if you are…
NORDVPN GUIDES
Does NordVPN Work With HBO Max? Here’s What You Need to Know
A VPN (virtual private network) is a great way to bypass geo-restrictions and access content that would otherwise be unavailable…
STREAMING GUIDE
Understanding Geo-Blocking: How It Works and Its Implications
What is Geo-Blocking? Geo-blocking refers to the practice of restricting access to internet content based on a user’s geographic location. It is a digital boundary that allows content providers to…